Category: IOT/OSINT/SCADA
Points: 200
Description:
A customer suspects that his email account is being targeted to be hacked. He has asked you to investigate and trace his attacker's real name (flag).
During your talk, he mentioned a suspicious email that he received about a bank transfer from someone he doesn't know. He actually tried to investigate by himself and found out the email was crafted to hide the real sender. He was able to go as far as finding a related facebook account by adding "tmctf" to the name he found from the email and that was as far as he got. Unfortunately he deleted the email after this, thinking it was just a random phishing email. He provided you with pcap logs from his machine to start your investigation.
ZIP password : virus
Download the file (https://s3-ap-northeast-1.amazonaws.com/trendmicro-ctf-2017/Pi1T3ou0CquyBbYosgng/files18.enc)
Decrypt the downloaded file by the following command.
> openssl enc -d -aes-256-cbc -k PYJU8G1k0fNKwacSJghz -in files18.enc -out files18.zip -md md5
> unzip files18.zip
Investigation
Let’s start by issuing a unzip pcap_record.zip. Loading up the pcap in wireshark, you can filter for pop and look at mail.
Looking through the mail packets, we can see this tcp.stream eq 307 looks interesting. Let’s follow that.
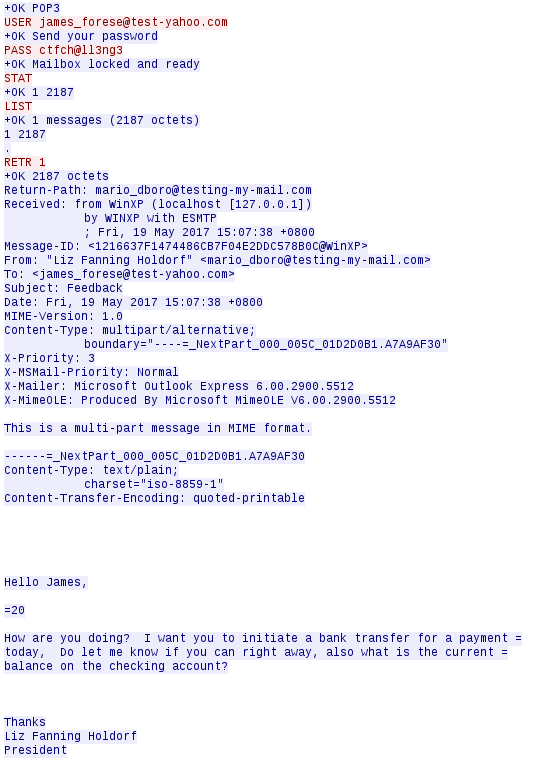
We’re told that there’s a facebook page related, so let’s search for mario dboro tmctf on facebook.
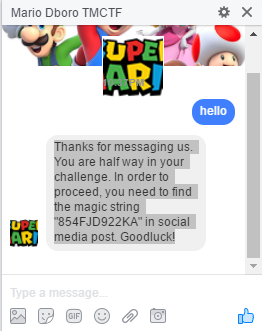
From here we can see he belongs to tmctfcommunity, so let’s message that page and see what happens.
“Thanks for messaging us. You are half way in your challenge. In order to proceed, you need to find the magic string “854FJD922KA” in social media post. Goodluck!”
I searched facebook for this string with no luck. So I took to twitter, my favorite social media network. I made the following google query: site:twitter.com "854FJD922KA", which yielded https://twitter.com/dboro18673.
There were many tweets that were possibly interesting here, and I’ll let you know that I certainly exhausted every single one of those links.
Tweets of Interest
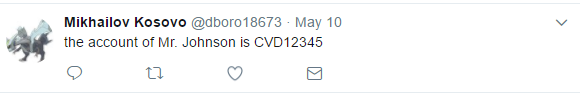
“the account of Mr. Johnson is CVD12345”
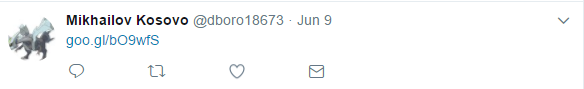
This link (goo.gl/bO9wfS) takes us to https://pastebin.com/71KhaaMK
Contents of pastebin. Pastebin is posted by Johndeculayan. email address of interest: [email protected]
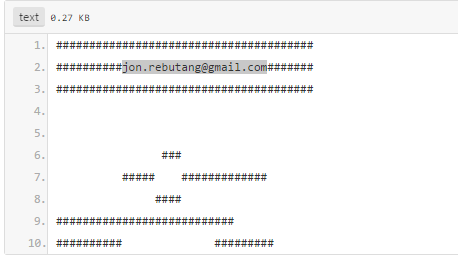
He links to this website http://texttt-01.super-schlank2013.org/
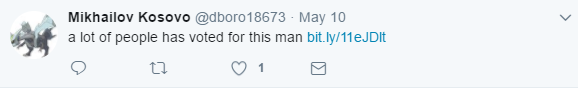
“a lot of people has voted for this man http://bit.ly/11eJDlt”
List of possible names
I was keeping a running list of possible names that this person could be, as well as a note to remind me where that name came from.
Liz Fanning Holdorf (fake email name)
Mario Dboro (facebook name/email name)
Mikhailov Kosovo (twitter name)
Jon Rebutang (pastebin contents)
John Deculayan (pastebin username)
Mr. Johnson
After like 2 hours of banging my head against the keyboard, I realized that I hadn’t seen any linkedin yet tonight, and so I took to linkedin.
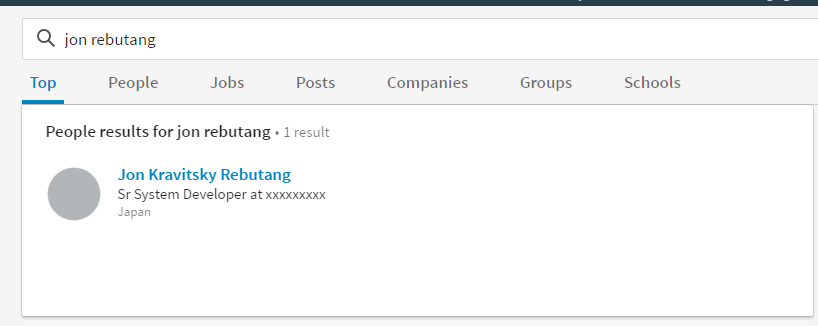
Now we have Jon Kravitsky Rebutang, let’s give that a shot as the flag.
Flag
TMCTF{Jon Kravitsky Rebutang}